MONUMENT — Nearly a year after a parent in the Lewis-Palmer School District 38 brought student data security concerns to district staff and the subsequent finding that a vulnerability existed, the district continues to deny there was ever an issue and launched a criminal investigation into the whistle blower.
Lewis-Palmer School District 38 Board of Education President Mark Pfoff did not respond to a Complete Colorado email about the issue, but has stood behind his belief that there was no data breach in posts on several Facebook pages.
However, a criminalist in forensics who deals with cyber security for the Weld County Sheriff’s Office disagrees, adding most businesses who are victims of such breaches will try to minimize the public damage by creating a definition of breach that doesn’t fit their specific situation.
“It depends on how it’s defined,” said Detective Daren Ford when asked if the Lewis-Palmer situation fit the definition of a breach. “If you define it as someone collected the data and used it inappropriately, then a breach hasn’t occurred. But if I have an environment that someone can get in and do something with — that to me would be a breach.”
Ford, who investigated a similar situation in Weld County several years ago, said breach is best defined as the ability to gain unauthorized access to data through a means that is unsecured or improperly secured.
THE BREACH:
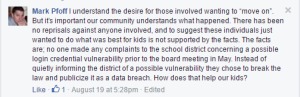
Pfoff and the district continue with a narrative that there was unauthorized access because students and parents shared their passwords with others. That was not the issue.
In its original report, Complete Colorado did not outline how the breach worked because the district had not taken steps to secure it. However, because the school district has since changed the way it manages access, Complete Colorado can explain the vulnerability that left thousands of students and their families open to identity theft or worse.
The district uses Google Apps for Education (GAFE), a hosting solution by Google that incorporates Google mail, calendar, and chat services. Lewis-Palmer used it for student email accounts, which at that time consisted of the student’s district identification number. system used by the district allowed anyone with email address in the system to download a complete contact list of district students. The list identified students’ names and district email addresses. Because student email accounts were comprised of the student ID, anyone who gained access to this list only needed to know the students’ birthdays to access another program, Infinite Campus, which contains the personal data of possibly thousands of students.
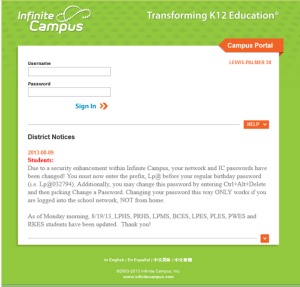
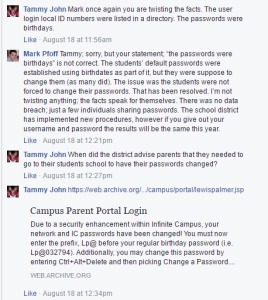
Pfoff and others maintain there was additional knowledge needed to gain access or “advanced cracking skills,” but they have not addressed the fact that information was provided by the district on the home page of the Infinite Campus website for nearly three years. On Aug. 9, 2013 the district posted: “Due to a security enhancement within Infinite Campus, your network and IC passwords have been changed! You must now enter the prefix LP@ before your regular birthday password (i.e. LP@031794).”
It is unknown how many contact lists were downloaded and shared over that time. But the district only contracted for the last year to be scrutinized.
THE TIMELINE:
Fall 2015: Lewis-Palmer parent Melinda Zark speaks to the district’s top two information technology staff members and a school principal about an issue with GAFE and how information obtained through GAFE compromised another software program used by the district, Infinite Campus.
Infinite Campus is a program that stores personal and academic information about students in the district. Many districts use the system, but individual districts are free to decide how much information is accessible to parents and students online.
In Lewis-Palmer, students and parents had access to names, addresses, and phone numbers for students, parents, siblings, and emergency contacts; schedules; attendance records; grades; locker numbers and combinations; transportation details, including where and when bus pickups took place; and health records. Zark said she was told there was nothing the school district could do about it.
December 2015: An unknown party emails Lewis-Palmer with similar concerns.
In the email obtained by Complete Colorado, the author writes, “I have heard that (name redacted) has somehow accessed your computer system, and is able to pull up multiple students’ private information on her phone. She pulls up their grades and then uses them in class to show people and humiliate the students. Apparently (name redacted) is one of the students whose grades are being displayed, which is why someone notified me. Please investigate immediately.”
Nothing was changed with the log in and passwords.
May 19, 2016: Zark attends a Lewis-Palmer Board of Education meeting and asked again for the district to address the issue. “You have a lot of computer experience,” Zark said to Pfoff, who is a former police detective specializing in cybercrimes and computer forensics and now runs his own cybersecurity firm. “I have a lot of information here that I don’t want to have. I’m very upset that this has been out here for so long. Please shut this down and discuss how you can make this better for all the students.”
At the same meeting, Lewis-Palmer parent Derek Araje discusses his concerns about the same issue during a break with Dewayne Mayo, a technology teacher in the district.
Complete Colorado obtained an audio clip of the conversation between Araje and Mayo, and Mayo can be heard being defensive with Araje. Araje repeatedly tells him that he has not broken into any accounts, just that the vulnerability exists and he wants the district to secure it.
Mayo gets mad and threatens to turn Araje over to the authorities. Mayo then says he knows the person that set up the system and is going to ask him about it. The recording ends with Araje asking him to please do that and find out who, if anyone, has accessed Araje’s daughter’s account.
“OK, I’ll find out for you,” Mayo says to end the conversation.
May 20: Mayo sends an email to the district superintendent, technology Department, and human resources in which he immediately labels Araje as the problem and describes the conversation as being so ugly that he had to “excuse myself from his rantings.”
“Unbeknownst to me he has a reputation,” Mayo wrote. “He voiced his concerns about GAFE and IC, but more to the point he admitted that he could obtain or get access to any student’s records in the district because of our lack of security protocols. … I am concerned that his rantings will pollute/influence those persons who are skeptical of any technology used in the district. Please let me know if there is any way I can be part of a positive solution.”
Chris Mack, district technology operations manager, responds that “(Araje’s) input could be valuable if he were in a position of wanting to assist the district. If he truly feels that we have a vulnerability, I would be interested in hearing what it is,” Mack said. But Mack goes on to say that he doesn’t believe that accessing student information was possible without “advanced cracking skills.”
Superintendent Karen Broft also dismisses the idea of a security breach. “I don’t believe that this is accurate,” she said in an email.
No one from the district ever contacted Araje about the issue, and nothing changed with the log in and passwords.
May 24: Complete Colorado publishes an exclusive report on the breach.
May 25: More than six months after the vulnerability was brought to the attention of the district, the district notified parents that there was a possible breach. In that notice, the district claimed they found the issue during “normal monitoring of IP addresses.” The district also shut down the student portal access to Infinite Campus.
May 27: The school district shuts down the both GAFE and Infinite Campus and files a criminal complaint against Araje with the Monument Police Department for computer hacking.
June 14: The district hires Boulder-based Applied Trust to investigate the extent of the problem for the past year, despite the fact that the vulnerability had existed since August 2013. The contract estimate was for $13,125. It is not known yet what the final cost was. The district has paid $350 to date.
June 20: Monument Police Department clear Araje of any wrongdoing.
Aug. 19: Applied Trust issues its report that says “a vulnerability was found due to an unintentional information disclosure from another application that was being tested (Google Apps). The student ID numbers were present in the ‘all contacts’ view of the Google application. This combined with the knowledge that student passwords for the other application were typically tied to the birthdate for the first login, could have provided access for an unauthorized user to log into an account.”
The company determined that any information obtained “was not used maliciously and the student accounts were not modified or deleted by any unauthorized user. No evidence of other student accounts show any compromise.” The report did not examine what may have occurred during the school years 2013-14 and 2014-15.
THE FALLOUT:
Despite all the evidence that Lewis-Palmer leaders knew of a serious vulnerability in a system holding private information about thousands of students, the district did little to address parental concerns or calls for change.
It took more than seven months for the district to investigate the idea that its system could be compromised. And although it is now clear that there was a problem, Pfoff and some in the community continue to deny the issue and point fingers at certain parents, including Araje. They also question the fact that according to the police report, Monument police cleared Araje without ever questioning him.
Araje says he’s sick that anyone would think he would do anything that would compromise other students’ information. He was only trying to get the district to make needed changes, he says.
“I was pretty outraged when I found out that my daughter’s picture, her bus stop, her locker number, her combination, and all of her private information was available for people to see,” Araje said. “I thought that was very dangerous for everybody in the community’s kids. So I thought this has to stop and this has to stop right now.”
He said he didn’t initially plan to say anything to anyone because Zark had spoken out. He thought the issue was so urgent and so dangerous that the district would do something immediately. When that didn’t happen, he began to push the issue.
“And then at that meeting I spoke to anyone who would listen to me,” Araja said. “And the reaction from everyone was no reaction. Even the head of technology said to me, ‘Well yeah, I know you can do that, but I know you won’t. Maybe we’ll look at fixing that next year.’”
Araje said the personal attacks have weighed on him and his family. “My wife never wanted to be out there,” Araje said. “She didn’t want to have us in the public eye. But when I saw this, I thought it was bigger than me. It was bigger than my reputation. And when I realized they weren’t doing anything at all and didn’t even show me any indication they would look into it, I felt everyone had to know.”’
He said he may have thrown caution to the wind, but students’ personal information wasn’t safe and he felt he needed to do something. And he would do it all again, with only one change: “I’d be much more forceful, go to more people within the district, until I found a group of people who cared.”
Ford said considering how long the vulnerability existed, the school district has been fortunate not to have encountered major problems. “Obviously it was a poor business practice that could have drastic effects,” Ford said. “It is extremely dangerous with kids involved. You have medical information and possible HIPPA violations as well. The fact they didn’t come across it or do anything with it, the district just got lucky.”


